2022-11-08
Does Code Signing Certificate protect against ransomware?

What is Code Signing Certificate?
Code Signing Certificates on the surface may seem like a tool used only by software developers. However, even an ordinary user can benefit from the fact that software that is downloaded to a computer bears such a certificate.
What is Code Signing Certificate used for?
Code Signing is a digital certificate that is used to sign a code. The importance of such a certificate is so great that each issuance of a certificate of this type is preceded by a detailed verification of the person or organization to which it is to be issued. The company’s length of existence in the market, its reputation and whether those applying for the certificate on behalf of the company have the right to do so are verified.
How does Code Signing work?
Certificates have a key role in protecting the user, who when installing software on a computer is immediately able to verify that the software provider is certified, and thus its identity and reputation have been confirmed by an independent entity – the Certification Center. To check the certificate at the time of software installation, select “Show publisher certificate information”.
The example of a certificate:
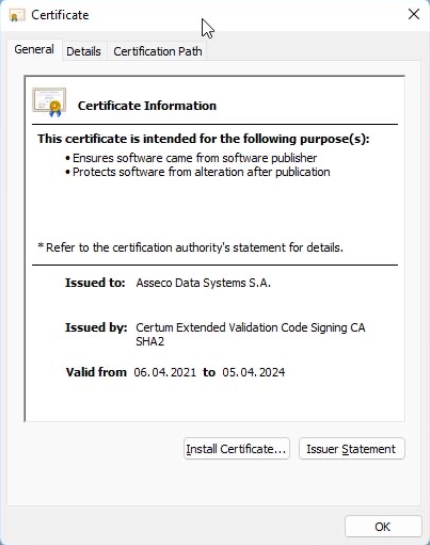
As you can see in the figure, the installed software has been signed with Code Signing of the highest level of validation. Such certificates can only be obtained by companies that have been on the market for more than 3 years and have a bank account.
Code Signing and ransomware
Certificates protect users who are able to verify the identity of the program provider, which prevents the accidental download of malware such as ransomware.
Ransomware is malware that, when downloaded to a computer, is able to encrypt the entire drive so that it is impossible for the user to read it. The attacker’s goal is to extort a ransom. The victim is told that after paying the ransom, the attacker will hand over a key to decrypt the drive. The fee is usually to be paid in bitcoins to make it impossible to trace the attacker. However, paying the ransom does not provide any guarantee of recovering data from one’s computer.
Of course, it is not only individuals who are vulnerable to ransomware attacks, as statistics compiled by Sophos show that up to 77% of Polish medium and large enterprises experienced such attacks in 2021. And 8 out of 10 attacks ended in data encryption, with as many as half of the companies deciding to pay a ransom to the criminals.
How does Code Signing protect against ransomware?
Of course, it is not the case that the use of Code Signing alone guarantees software security. It can happen that criminals obtain such a certificate and sign malware with it. Certification Centers, upon receiving such information, are obliged to immediately revoke the certificate. In this way, further signing of malware will be prevented.
Always verify that the software is signed with a certificate before installing it. If it is not, it is a good idea to give up the installation and not risk infecting your computer with malware that is not easy to get rid of. You should regularly back up your most important data, such as files necessary for your work or diploma thesis. If malware is installed, you will save a lot of nerves and will not be forced to pay the ransom to regain access to your data.
Only a valid certificate protects the code
And if you develop the software yourself, remember to have a valid certificate to sign the code and time-stamp the signature, which will increase users’ trust in your software.