2025-12-16
Transition to shorter SSL/TLS certificate validity periods
Key information
Starting March 15, 2026, SSL/TLS certificates will have shorter maximum validity periods. This change will be introduced in stages: the limit will be reduced to 200 days in 2026, 100 days in 2027, and finally 47 days on March 15, 2029.
Important: The products Certum offers remain unchanged. However, individual certificates issued within these products must comply with the validity limits in effect at the time of issuance.
This means certificates will need to be renewed more frequently. To avoid service interruptions, organizations will increasingly rely on automated certificate issuance and renewal.
This change applies to all SSL/TLS products:
- Certum Commercial SSL (DV),
- Certum Trusted SSL (OV),
- Certum Premium EV SSL (EV).
Key dates
How to prepare?
Organizations should begin preparing now to ensure business continuity. Manual certificate handling will quickly become inefficient and risky – especially once certificates are limited to around 100 days or less.
Recommended actions include:
- Train your teams – Make sure IT staff understand the timeline, requirements, and practical implications of these changes.
- Discover all certificates – Perform a thorough inventory of every SSL/TLS certificate used across your systems – including websites, internal services, APIs, load balancers, devices, and applications.
- Implement monitoring – Set up automated alerts for certificate expiration. Ensure that notifications reach the right people and allow enough time for corrective action.
- Automate certificate lifecycle – Introduce automated issuance and renewal mechanisms (e.g., ACME protocol). Certificates with short validity periods will require reliable automation to prevent outages.
- Evaluate your processes – Review existing procedures, test automation flows, and address any approval delays or infrastructure bottlenecks.
- Identify systems that cannot yet support automation – Plan how to update or replace legacy systems that rely on manual certificate management.
- Ensure your contact e-mail is valid and monitored – Certum sends renewal notifications and expiration reminders to this address. With shorter certificate validity periods, missing these messages increases the risk of unexpected outages.
Important: Most organizations need several months to implement automation effectively. Starting early helps avoid disruptions.
What will happen to SSL/TLS certificates after the transition?
Certificates issued before each key date will remain valid until their expiration dates. The issuance date (not order date) determines the validity period. Application processing times for OV and EV certificates may vary, so plan renewals early to ensure smooth continuity.
After each key date, new certificates will comply with the updated validity periods:
- before March 15, 2026, valid for up to 398 days,
- between March 15, 2026, and March 15, 2027, valid for up to 200 days,
- between March 15, 2027, and March 15, 2029, valid for up to 100 days,
- after March 15, 2029, valid for up to 47 days.
If the issued certificate has a shorter validity period and expires before the end of your product’s validity, you can use the reissue process to take full advantage of the validity available under your product.
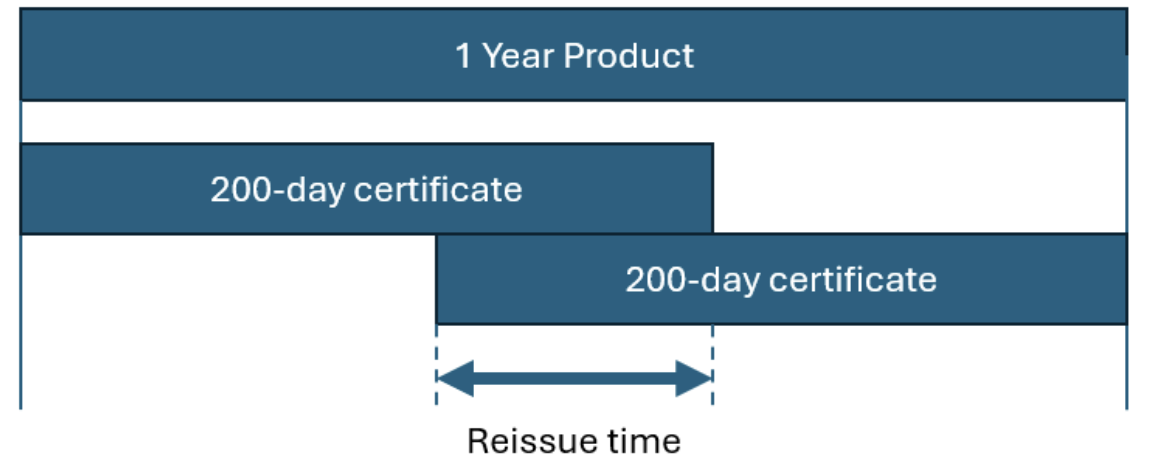
Example: If you purchase a 1-year SSL product and the certificate is issued on March 15, 2026, it will be valid for 200 days. To use the full year of your product, simply reissue the certificate once between day 165 and day 200 – this will give you complete coverage for the entire year, split across two certificates.
When you reissue any certificate after March 15, 2026, the new certificate must comply with the validity limits in effect on the reissue date.
Domain validation reuse periods are also being shortened alongside certificate validity periods. This means that when you reissue a certificate, domain revalidation may be required if the previous validation has expired. Plan your reissues accordingly to avoid delays.
Why is this changing?
These changes, approved by the CA/Browser Forum in Ballot SC-081v3, are designed to improve the security and reliability of digital identities on the internet.
Key reasons include:
- Enhanced security – shorter validity periods enable more frequent key rotation, reducing the risk associated with compromised keys.
- Faster adoption of new standards – frequent renewals encourage quicker implementation of updated cryptographic algorithms and security standards.
- Reduced vulnerability window – attackers have less time to misuse a compromised or misissued certificate.
- Simplified revocation – shorter validity periods reduce reliance on complex revocation systems, as compromised certificates expire sooner.
- Improved operational security – more frequent renewals reduce the risk of outdated configurations and limit the impact of human error.
- Reliability of certificate information – certificate data is revalidated more often, ensuring it stays accurate and trustworthy.
Who will be affected the most?
- Organizations with large numbers of certificates – especially those without a centralized management process.
- Teams relying on manual renewals, spreadsheets, or email reminders.
- Environments using short-lived infrastructure, such as microservices, containers, or dynamic cloud workloads.
- Companies operating customer-facing services with strict uptime requirements (banks, SaaS, telecom, ecommerce).
- Organizations with multiple brands or domains, where renewals are distributed across different teams.
- Legacy systems that do not support automated certificate renewal.
Related links:
Certificate Discovery is now available in CertManager
How to activate Certum SSL certificate using ACME?
How to use Certbot to issue Certum SSL ACME certificate?
Transition to shorter Code Signing certificate validity periods