2021-08-09
Phishing – how to protect yourself against it?

Phishing is currently one of the biggest threats to Internet users. What to do if it happens to you? How to protect yourself against it? Is a green padlock enough? And finally, what can be done to recognize it effectively? Read our article to find out.
1. What is phishing?
2. Modern examples of phishing
3. Phishing and SSL certificates
4. Phishing – methods of protection
5. What to do if you recognize phishing?
6. Summary
1. What is phishing?
Phishing is a term that has been used since the 1990s. It was first used in the hacker magazine “2600”. The term can be translated in two ways – “password harvesting fishing” or a combination of the words “fishing” and “phreaking”. This is nothing more than an attempt to impersonate a person or institution in order to obtain benefits such as bank account passwords, BLIK codes for transactions, social media passwords, online payment authorization codes, or cash directly. Initially, phishing occurred mainly in the form of emails, with the most popular being the so-called Nigerian prince scam. These types of frauds were known even before the Internet became popular. They were then known as the “Spanish prisoner” and victims of this fraud, which dates back to the 19th century, had the impression that they had been corresponding with a wealthy aristocrat wrongfully imprisoned and in need of help. Victims were lured with promises of payment and sometimes even marrying the aristocrat’s beautiful daughter for initially small financial help. After paying more and more money, it turned out that neither a rich prisoner nor, more importantly, a generous payment for help existed . With the rise of the Internet, the “Spanish prisoner” has evolved into the “Nigerian prince scam”, which has taken the form of an email message from an African prince, a descendant of a murdered opposition member, and other wealthy individuals who, for some reason, needed to transfer their fortune to the recipient of the email.
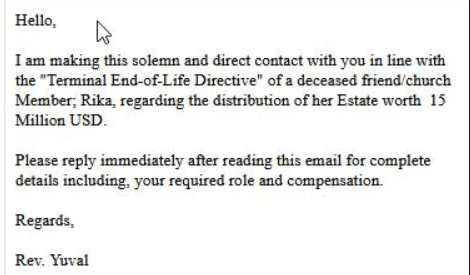
Fig. 1 Example of Nigerian fraud
In subsequent messages, once contact is made, the potential victim would be asked to send a small amount of money to be used, for example, to prepare the documents necessary to complete the transaction. Nowadays, when most popular email boxes automatically qualify such messages as SPAM, the probability of success of such an attack is quite low, which does not mean that the phishing threat has decreased. Moreover, in the age of social media and widespread digitization of services, we can encounter phishing almost everywhere.
2. Modern examples of phishing
Have you ever received a strange message from a friend on Facebook who you have not heard from in a few years? It is likely that the message contained a link to some suspicious website where you had to fill out a form. Or maybe a long-lost friend has unexpectedly asked you for help in the form of a BLIK code, because his/her banking application did not work that day? Regardless of whether you fulfilled the request of your “friend” or not, you experienced phishing. With the development of social media, new ways have opened up for frauds who, with a few clicks, can try to get you to give them money via bank transfer or premium SMS services. How does this happen? All a fraud has to do is create another account on a social networking site using publicly available data taken from a search engine, thus creating a twin account similar to yours. If you have a publicly available list of friends they can also send messages or invitations to them. A fraud may also have gained access to your friend’s real account if they obtained it through another phishing attack or leak from other websites. If you receive this type of message, it is recommended to check if it comes from an account of one of your friends, and if you receive an invitation, check if this person has been added by you before. Under no circumstances should you click on links. If you suspect that this person really needs help, just call them.
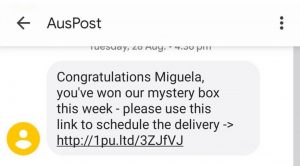
Fig. 2 Example of phishing on Facebook
One of the most popular and also most dangerous examples of phishing are emails impersonating a bank. Realistic-looking messages telling you to urgently log in to your account to update your details, accept the terms and conditions etc., under the threat that if you fail to do that, your account will be blocked – you will lose the possibility to use your funds. This fraud is particularly dangerous precisely because it involves money – and who among us would risk the possibility of losing all of their funds accumulated in a bank account? Such messages most often contain a link to a fake bank login page – it may look identical to the real page of your bank – after entering the data on it, most often we get an information about the necessity of SMS confirmation. At this point, most often, a fraud logs into the bank in the background using the credentials received from you, and the SMS is used to authorize the addition of the fraud’s account to the trusted recipients, so that they can take all the money out of your account a few moments later without any confirmation on your part.

Fig. 3 A fake bank website that looks identical to the real one. Source: Deutsche Bank
Frauds impersonating transaction services have also gained popularity recently. The most popular of these are attempts, unfortunately often successful, to defraud on the Polish transaction portal OLX. A person who listed an item was contacted within a very short time, usually via the WhatsApp messenger, by a person who informed in broken Polish that they decided to buy the item and asked whether it was possible to pay through a “secure OLX transaction”. Unaware sellers, probably guided by the wording “secure”, agreed to this form. At this point, the fraud sent a link to a page that assured that the money had already been transferred by the buyer, and that the following information needed to be provided to receive it:
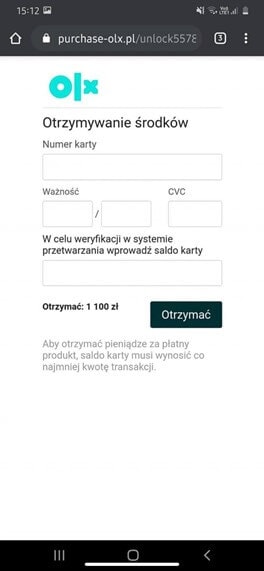
Fig. 4 Fake transaction on OLX
As you can see, the data needed to “authorize receipt of funds” is the card number, expiration date and CVC code – that is the necessary data from the card. In addition, to make things easier for themselves, the frauds also asked to enter the account balance – so they could take out all the money at once. In the previous steps of the attack, the victim also provided his/her personal details, i.e. first name, last name and address – after all, the form was supposed to enable ordering courier delivery to the buyer. As a result of this attack, the transaction was not realized and the victim was robbed of all their funds.
Of course, in addition to the above examples, there are plenty of others based on phishing methods, in the form of websites claiming to be forms from courier companies, transport companies, etc.
As you can see, even though it has been a long time since the first Nigerian scam, phishing attacks still rely on the same thing, primarily on the gullibility of the victims and the desire to benefit quickly – send a text message to get a discount, log in and fill out a form to win a prize, enter your details to get the money that’s already waiting for you. So how to protect ourselves from such attacks?
3. Phishing and SSL certificates
The first thing that comes to mind when checking if a website is trying to impersonate an institution we trust is to verify if it has an SSL certificate. That is a great idea. But will it be enough?
SSL certificates are divided by the number of domains they contain (single domain, multidomain, wildcard) and by the validation level (DV – Domain Validation, OV – Organization Validation, EV – Extended Validation). There are certification centers in the market that only issue certificates that undergo basic domain validation. These are the certificates that are easiest to obtain and thus are often used for phishing attacks. According to 2019 data, about 94% of phishing websites worldwide that were secured with an SSL certificate had a DV certificate.
Thus, if you suspect a website of phishing, simply checking if the website has an SSL certificate may not be enough, especially if it has a DV certificate. It is worth paying attention to, because the bank’s website should always have an EV certificate in the place where you enter your login data. The graphic below shows how to recognize this.
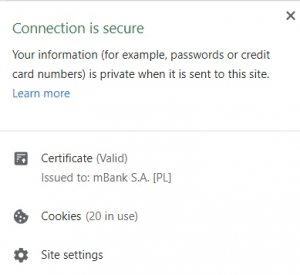
Note that the certificate shows the name of the organization on the left. This means that it is an extended validation certificate. Extended validation means that the certification center issuing the certificate has verified the existence of the organization including its address and whether the person acting on behalf of the company has the authority to do so.
Certum, before issuing an SSL certificate, also actively checks that the particular website for which the certificate is issued is not being used to mislead users through internal mechanisms that verify the status of each website. If verification indicates that there is suspicious content on the website, Certum staff will contact the client to clarify the matter. Many times, customers do not even know that their websites have been hacked and their content swapped for phishing content.
4. Phishing – methods of protection
We already know what phishing is and how to protect against it in terms of SSL certificates. What other methods of protection can be used?
If you have any suspicion that you may have been misled:
- Check the SSL certificate on the website – you can do this easily in the address bar of your browser, if the website has an OV or EV certificate you may assume that the website is not used for fraud.
- Check the website address – frauds often use addresses that are confusingly similar to the original e.g. the original Santander bank login page is https://www.centrum24.pl/, frauds could use https://www.centrunn24.pl/ – two ‘n’s instead of an ‘m’.
- Do not click on links from suspicious emails – if you are in any doubt about the messages you have received call the helpline.
- Pay attention to the language used in messages – those that are attempts to attack often contain typos, syntax errors or spelling mistakes.
- Check the email addresses from which you receive messages – information from the bank should come from addresses in the bank’s domain.
- Do not provide out your passwords and card numbers if you are not sure if the website is secure.
- Do not provide data that is redundant – your bank or transaction service will never ask you about your account balance.
- Use two-factor authentication where possible – password + SMS.
- Carefully read the text messages that authorize bank transactions.
- Turn off the Premium SMS service on your phone.
- Use password generators – even if a password from one service is leaked, a fraud will not be able to log into other services you use.
To protect yourself from phishing, you should first of all carefully read all the information on the websites. If you have doubts, you can always use the hotline or read the terms and conditions. Remember that websites that offer goods for suspiciously low prices or even luxury goods for free are mostly frauds.
5. What to do if you recognize phishing?
When you have checked the certificate (or lack thereof) as well as the web address, and you are sure that the website requires way too much data from you than it is needed – it was probably an attempt at fraud.
However, should you leave such information only to yourself? How about letting others know that such a fraud is circulating online?
You can do this in several ways:
– via https://www.phishtank.com/ – here you can also check whether a given website has already been reported as phishing.
– https://incydent.cert.pl/ – you can anonymously report suspicious website, email and other impersonation attacks.
– to the certification center that issued the certificate for the domain that is suspected of being fraudulent. The certification center will handle the matter immediately, clarify the situation with the client or revoke the certificate for such domain. At Certum you can report such information via our hotline or form: https://pomoc.certum.pl/pl/cert_wiedza_unizewaznienie_ev
It is also a good idea to let your friends know, especially older people who may not be up to date on online threats.
6. Summary.
Unfortunately, the so-called green padlock is not always a guarantee that you will not be a victim of a threat. In an age when web browsers mark all websites without an SSL certificate as “untrusted”, frauds have found a way to obtain those certificates as well. Keep in mind that if a certificate is issued and malicious content is published on the website after the certificate is issued, the Certification Center is not always able to control this. Always check the website address, verify that the messages sent to you come from trusted sources and, above all, apply the principle of limited trust whenever something seems suspicious.
D. Lubowiecki “Legal and criminal issues of phishing, with particular emphasis on the Internet banking” (original title: Prawno-kryminalistyczna problematyka phishingu, ze szczególnym uwzględnieniem środowiska bankowości internetowej) Kwartalnik Prawo-Społeczeństwo-Ekonomia 1/2017 p. 30,
antykorupcja.gov.pl “”Hiszpański więzień” pierwowzorem listu z Nigerii” [accessed on 29.07.2021].